THE COMPLETE ENTERPRISE SOLUTION
Industry leading complete cybersecurity platform.
Discover your vulnerabilities instantly with automated network penetration testing seamless deployment. One click. You're protected.
THE COMPLETE ENTERPRISE SOLUTION
Industry leading complete cybersecurity platform.
Discover your vulnerabilities instantly with automated network penetration testing seamless deployment. One click. You're protected.
Assets targeted
All Assets
20
IPs
12
Domains
19
Subdomains
46
TOTAL
Processes
All Processes
by Status
by Type
by Project
Blackbox Internal
16
Greybox Internal
8
Greybox Internal
14
BlackBox External
9
Greybox External
2
Digitalis Bank
OVERVIEW
Dashboard
Processes
Vulnerabilities
Assets
Digitalis Bank
PROJECTS
Search for Projects..

Cloud
2

Web servers
2

HQ Offices Inter..

loT local net..
2
Settings
New Process
New Project
Digitalis Bank
Dashboard
All assets
All projects
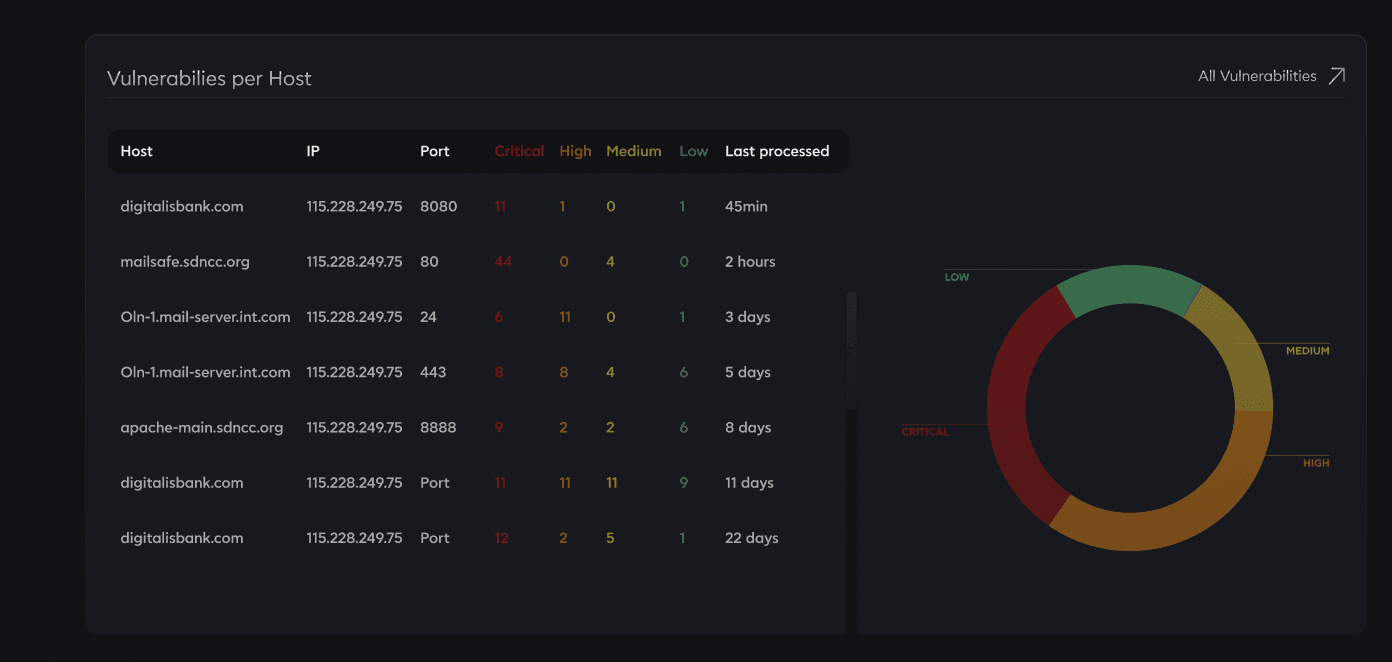
Vulnerabilities by severity
All Vulnerabilities
18
18
18
Critical
39%
11
11
11
High
34%
25
25
25
Medium
22%
11
11
11
Low
5%
8
8
8
Informational
39%
41 Total
Nov 20 - Dec 20, 2024
JD
Steven
Maarten
139
Assets targeted
All Assets
20
IPs
12
Domains
19
Subdomains
46
TOTAL
Processes
All Processes
by Status
by Type
by Project
Blackbox Internal
16
Greybox Internal
8
Greybox Internal
14
BlackBox External
9
Greybox External
2
Digitalis Bank
OVERVIEW
Dashboard
Processes
Vulnerabilities
Assets
Digitalis Bank
PROJECTS
Search for Projects..

Cloud
2

Web servers
2

HQ Offices Inter..

loT local net..
2
Settings
New Process
New Project
Digitalis Bank
Dashboard
All assets
All projects
Vulnerabilities by severity
All Vulnerabilities
18
18
18
Critical
39%
11
11
11
High
34%
25
25
25
Medium
22%
11
11
11
Low
5%
8
8
8
Informational
39%
41 Total
Nov 20 - Dec 20, 2024
JD
Steven
Maarten
139
Vulnerabilities by severity
All Vulnerabilities
18
18
18
Critical
39%
11
11
11
High
34%
25
25
25
Medium
22%
11
11
11
Low
5%
8
8
8
Informational
39%
41 Total
Assets targeted
All Assets
20
IPs
12
Domains
19
Subdomains
46
TOTAL
Processes
All Processes
by Status
by Type
by Project
Blackbox Internal
16
Greybox Internal
8
Greybox Internal
14
BlackBox External
9
Greybox External
2
OVERVIEW
Dashboard
Processes
Vulnerabilities
Assets
Digitalis Bank
Digitalis Bank
PROJECTS
Search for Projects..
Cloud
2
2
Web servers
HQ Offices Inter..
loT local net..
2
Settings
All assets
All projects
New Process
New Project
Dashboard
Digitalis Bank
JD
Steven
Maarten
139
Nov 20 - Dec 20, 2024
Digitalis Bank
OVERVIEW
Dashboard
Processes
Vulnerabilities
Assets
Digitalis Bank
PROJECTS
Search for Projects..

Cloud
2

Web servers
2

HQ Offices Inter..

loT local net..
2
Settings
New Process
New Project
Digitalis Bank
Dashboard
Assets targeted
All Assets
20
IPs
12
Domains
19
Subdomains
46
TOTAL
Processes
All Processes
by Status
by Type
by Project
Blackbox Internal
16
Greybox Internal
8
Greybox Internal
14
BlackBox External
9
Greybox External
2
All assets
All projects
Vulnerabilities by severity
All Vulnerabilities
18
18
18
Critical
39%
11
11
11
High
34%
25
25
25
Medium
22%
11
11
11
Low
5%
8
8
8
Informational
39%
41 Total
Nov 20 - Dec 20, 2024
JD
Steven
Maarten
139
Digitalis Bank
OVERVIEW
Dashboard
Processes
Vulnerabilities
Assets
Digitalis Bank
PROJECTS
Search for Projects..

Cloud
2

Web servers
2

HQ Offices Inter..

loT local net..
2
Settings
New Process
New Project
Digitalis Bank
Dashboard
Assets targeted
All Assets
20
IPs
12
Domains
19
Subdomains
46
TOTAL
Processes
All Processes
by Status
by Type
by Project
Blackbox Internal
16
Greybox Internal
8
Greybox Internal
14
BlackBox External
9
Greybox External
2
All assets
All projects
Vulnerabilities by severity
All Vulnerabilities
18
18
18
Critical
39%
11
11
11
High
34%
25
25
25
Medium
22%
11
11
11
Low
5%
8
8
8
Informational
39%
41 Total
Nov 20 - Dec 20, 2024
JD
Steven
Maarten
139
ULTIMATE PEN-TESTING PLATFORM
Effortlessly secure & Impressively smart
Introducing MindTheHack – the future of cybersecurity. Our platform transforms network penetration testing into an experience. With MindTheHack, embrace intuitively simple, deeply insightful security.
ULTIMATE PEN-TESTING PLATFORM
Effortlessly secure & Impressively smart
Introducing MindTheHack – the future of cybersecurity. Our platform transforms network penetration testing into an experience. With MindTheHack, embrace intuitively simple, deeply insightful security.
ULTIMATE PEN-TESTING PLATFORM
Effortlessly secure & Impressively smart
Introducing MindTheHack – the future of cybersecurity. Our platform transforms network penetration testing into an experience. With MindTheHack, embrace intuitively simple, deeply insightful security.
Tailored Automation Workflows

Customize security like never before. Our platform's custom workflows let you automate essential security tasks seamlessly, ensuring strong defense layers in sync with your business operations.
Tailored Automation Workflows

Customize security like never before. Our platform's custom workflows let you automate essential security tasks seamlessly, ensuring strong defense layers in sync with your business operations.
Tailored Automation Workflows

Customize security like never before. Our platform's custom workflows let you automate essential security tasks seamlessly, ensuring strong defense layers in sync with your business operations.
Dynamic Command Center

Experience the ultimate control with our Dynamic Command Center. Dive into real-time security analytics, stay ahead of threats, and implement swift, decisive actions. Your security, under your command.
Dynamic Command Center

Experience the ultimate control with our Dynamic Command Center. Dive into real-time security analytics, stay ahead of threats, and implement swift, decisive actions. Your security, under your command.
Dynamic Command Center

Experience the ultimate control with our Dynamic Command Center. Dive into real-time security analytics, stay ahead of threats, and implement swift, decisive actions. Your security, under your command.
Simplified Project Management
With our intuitive interface, managing security projects becomes effortless. Activate automated response protocols at a moment's notice, preserving your system's integrity amidst any challenge.
Simplified Project Management

With our intuitive interface, managing security projects becomes effortless. Activate automated response protocols at a moment's notice, preserving your system's integrity amidst any challenge.
Simplified Project Management

With our intuitive interface, managing security projects becomes effortless. Activate automated response protocols at a moment's notice, preserving your system's integrity amidst any challenge.
Sophisticated User Access Control

Elevate your security strategy with refined user access and permission settings. Our advanced management system empowers you to fortify your digital environment precisely and efficiently.
Sophisticated User Access Control

Elevate your security strategy with refined user access and permission settings. Our advanced management system empowers you to fortify your digital environment precisely and efficiently.
Sophisticated User Access Control

Elevate your security strategy with refined user access and permission settings. Our advanced management system empowers you to fortify your digital environment precisely and efficiently.
EXPLORE MINDTHEHACK
Core Features
Understanding your investment's value is crucial in cybersecurity. With MindTheHack, you're investing in a safeguard that delivers significant returns by protecting your business assets. Here's the cost-value advantage:
EXPLORE MINDTHEHACK
Core Features
Understanding your investment's value is crucial in cybersecurity. With MindTheHack, you're investing in a safeguard that delivers significant returns by protecting your business assets. Here's the cost-value advantage:
EXPLORE MINDTHEHACK
Core Features
Understanding your investment's value is crucial in cybersecurity. With MindTheHack, you're investing in a safeguard that delivers significant returns by protecting your business assets. Here's the cost-value advantage:

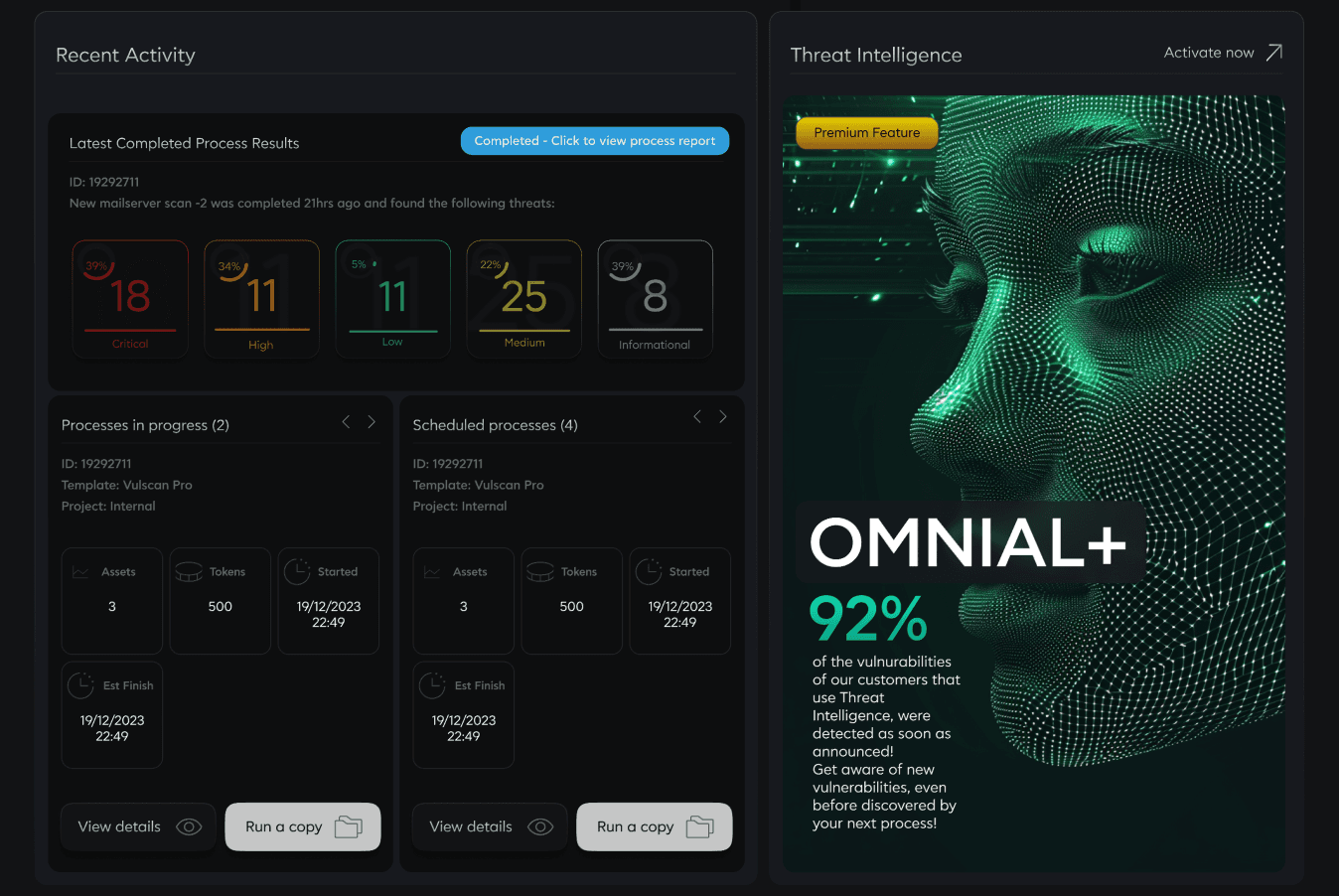
Automated Processes
Deploy our AI-driven tools for round-the-clock surveillance, detecting vulnerabilities with precision and speed.

Automated Processes
Deploy our AI-driven tools for round-the-clock surveillance, detecting vulnerabilities with precision and speed.

Automated Processes
Deploy our AI-driven tools for round-the-clock surveillance, detecting vulnerabilities with precision and speed.
Ethical Hacker Insight
Benefit from the intelligence of seasoned ethical hackers who deepen your defense strategies, simulating and thwarting real-world attacks.

Ethical Hacker Insight
Benefit from the intelligence of seasoned ethical hackers who deepen your defense strategies, simulating and thwarting real-world attacks.

Ethical Hacker Insight
Benefit from the intelligence of seasoned ethical hackers who deepen your defense strategies, simulating and thwarting real-world attacks.
Proactive Threat Mitigation
Stay ahead of the curve with preemptive actions against potential threats, reducing risk exposure and securing your business operations.

Proactive Threat Mitigation
Stay ahead of the curve with preemptive actions against potential threats, reducing risk exposure and securing your business operations.

Proactive Threat Mitigation
Stay ahead of the curve with preemptive actions against potential threats, reducing risk exposure and securing your business operations.
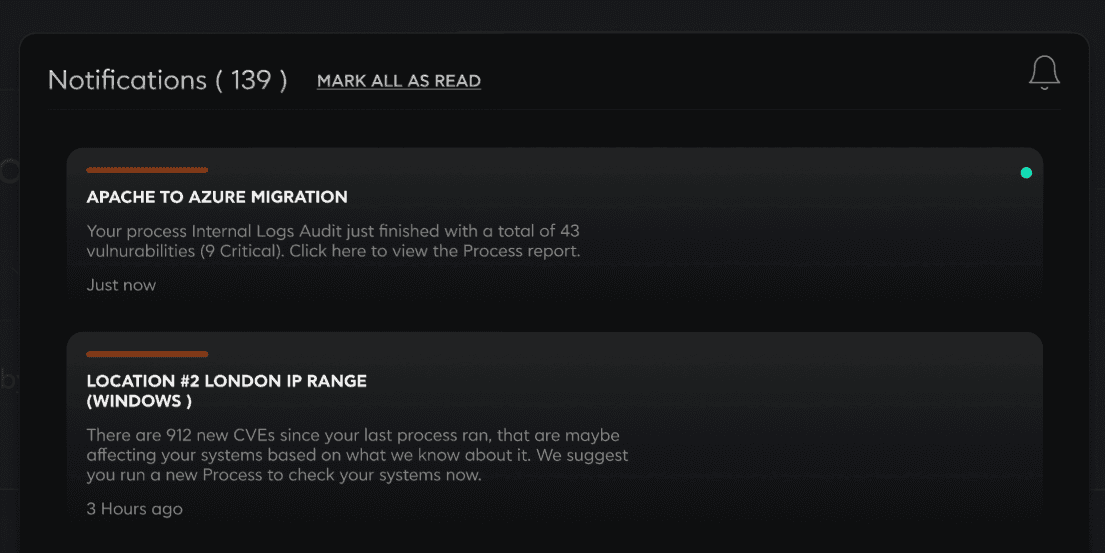
Real-time Alerts
Receive immediate notifications on potential breaches, enabling swift action and minimal disruption.

Real-time Alerts
Receive immediate notifications on potential breaches, enabling swift action and minimal disruption.

Real-time Alerts
Receive immediate notifications on potential breaches, enabling swift action and minimal disruption.
VIDEO PRESENTATION
Got 60 seconds? Let us show you what we can do!
Dive into our comprehensive feature set and discover how we're revolutionizing cybersecurity management in a concise video tour.
VIDEO PRESENTATION
Got 60 seconds? Let us show you what we can do!
Dive into our comprehensive feature set and discover how we're revolutionizing cybersecurity management in a concise video tour.
VIDEO PRESENTATION
Got 60 seconds? Let us show you what we can do!
Dive into our comprehensive feature set and discover how we're revolutionizing cybersecurity management in a concise video tour.

WE PLAY ALONG WITH OTHERS
Seamless integration
At MindTheHack, we understand seamless integration with your systems is key. Our platform is designed to work with a broad range of applications and services, ensuring a hassle-free, efficient transition to enhanced security.
WE PLAY ALONG WITH OTHERS
Seamless integration
At MindTheHack, we understand seamless integration with your systems is key. Our platform is designed to work with a broad range of applications and services, ensuring a hassle-free, efficient transition to enhanced security.
WE PLAY ALONG WITH OTHERS
Seamless integration
At MindTheHack, we understand seamless integration with your systems is key. Our platform is designed to work with a broad range of applications and services, ensuring a hassle-free, efficient transition to enhanced security.





API Integration
Easily connect Mindthehack with your existing infrastructure through our flexible API, enabling custom integrations and automated security processes.
Third-Party Plugins
Amplify your security with our support for third-party plugins, allowing for a tailored defense strategy with additional specialized security tools.
Ethical Hacker Insight
Benefit from the human intelligence of seasoned ethical hackers who bring depth to your defense strategies, simulating and thwarting real-world attacks.
Custom Integrations
Custom integration service is designed to seamlessly blend with your existing infrastructure, offering a tailored cybersecurity solution that adapts to your unique requirements.
FREQUENTLY ASKED QUESTIONS
Got questions? We've got the answers!
Here's a collection of the most common questions we have seen being asked. Got a specific need? Dont hesitate to contact us
FREQUENTLY ASKED QUESTIONS
Got questions? We've got the answers!
Here's a collection of the most common questions we have seen being asked. Got a specific need? Dont hesitate to contact us
FREQUENTLY ASKED QUESTIONS
Got questions? We've got the answers!
Here's a collection of the most common questions we have seen being asked. Got a specific need? Dont hesitate to contact us
What is MindTheHack and how does it protect my business?
Can MindTheHack be integrated with our existing IT infrastructure?
How does MindTheHack handle data privacy and compliance?
What kind of support can I expect from MindTheHack ?
How can I get started with MindTheHack and what are the costs involved?
WE ESTABLISH PARTNERSHIPS
Loved by organizations worldwide
WE ESTABLISH PARTNERSHIPS
Loved by organizations worldwide
WE ESTABLISH PARTNERSHIPS
Loved by organizations worldwide
LET'S TALK
Ready to experience the future?
Elevate your cyber defense strategy. Engage with us for a bespoke demonstration of MindTheHack and observe the unparalleled capabilities of our platform that safeguard your business against the forefront of cyber threats.



Copyright 2025 - MindTheHack®, All rights reserved.
LET'S TALK
Ready to experience the future?
Elevate your cyber defense strategy. Engage with us for a bespoke demonstration of MindTheHack and observe the unparalleled capabilities of our platform that safeguard your business against the forefront of cyber threats.



Copyright 2025 - MindTheHack®, All rights reserved.
LET'S TALK
Ready to experience the future?
Elevate your cyber defense strategy. Engage with us for a bespoke demonstration of MindTheHack and observe the unparalleled capabilities of our platform that safeguard your business against the forefront of cyber threats.



Copyright 2025 - MindTheHack®, All rights reserved.

























